Executive Summary
Identity fraud involves a case where a number of individuals use the identities of other people for the purpose of their financial gains. This may take a form where they take over other peoples accounts or even just decides to open up other new accounts in different people’s names. Currently, United Kingdom has been found to have a faster rate of growing in identity fraud, where according to the information provided by the Cabinet Office, it has been found out that identity fraud is costing the United Kingdom at least £1.3 billion on annual basis. Identity fraud has also been determined to be the most difficult fraud in the United Kingdom to fight. The reason to this is that the process of knowing that you are a victim of identity fraud takes long, about 14 months, making it harder to combat despite the fact that lenders are currently applying more sophisticated ways to spot all identity fraudsters (Best, 2004).
Introduction
Many people have not come to term to believe how it is always easy for other individuals with criminal intent can be able to access personal data and other information without physically breaking into homes and other facilities. Technology has played a significant role in providing a platform where such criminal acts are being carried out. For instance, within public places, most of the criminals may participate in shoulder surfing thus being able to watch other individuals from a location that is nearby. This can take place as the victim is punching in the keys on the telephone, punching in the credit card number or debit card number, or even listening to the conversation when giving out details of the credit-card to a rental car company or even the hotel. The identity fraudsters can even pose as business people, consultants, or even representatives from various organizations for the purpose of just extracting some information that will be of use to their act of stealing from innocent individuals who are not aware of what is going on. Therefore, this paper reports on the case of identity fraud, where fraudsters assume the identity of a victim and through all means he or puts in place decides to swindle the person or other individuals who are close.
Types of Identity Fraud
As it has been noted, identity fraud is considered to be the crime of applying someone else’s financial and personal information for financial gain. This could include information such as the driver’s license, an account number, Social Security number, or health insurance card information. The following are some of the types of identity frauds existing all over the globe.
- Medical Identity Fraud
This type of identity fraud is considered to be quite fatal, as one may end up having a lot of bills that have been sustained by the individual who stole the identity and also other issues that are considered to be quite personal. It is proved to be fatal because when a thief utilized another person’s identity, he or she is able to manipulate all important information in the medical files, and this may involve major altering of critical data. The impact turns out to be fatal when the real individual starts seeking for care, where he or she ends up with the wrong data on medical history, allergies, blood type, and other identity information. In most of the cases, identity fraudsters normally take personal information for financial gain by just filing fraudulent claims against the real person’s health policy. On the other hand, medical identity fraudster often uses personal information at the medical facilities, and such information can be the person’s Social Security and health-insurance number. Another way that such fraudster can access medical information is through hacking into the medical files database and doing everything to make sure that all information is changed for his personal purposes (Menninger, 2005).
The following are some of the reasons as to why many people are stealing other individuals’ medical information for their personal gain:
- Using inflated of fake treatment claims for the purpose of billing up the other person’s health plan. Some of these individuals are medical personnel or even doctors who have a better access to other individuals’ medical information and can use such data for the purpose of starting up their own fake clinics to earn more money.
- Using of another person’s identity when buying prescription drugs. Some may want to start a business of selling different prescriptions or even just use such prescriptions, such as narcotics, for their own purposes.
- Using medical identity information for getting free treatment. These medical documents are more often abused for this reason, as medical identity fraudsters do not really have their own health and other medical coverage. Therefore, they use another person’s identity for the purpose of getting free medical treatment that is normally based on the real person’s medical policy, and they achieve this by signing into any hospital or a medical clinic by using the real person’s identity and medical policy on the card receives the bills of the product and services offered.
Becoming a victim of medical identity fraud is quite easy, and one will normally find out that once large amount of bills have been built up in the real names account, they normally disappear without paying any amount of the bill, and thus leaving behind a case that is made to destroy the credit card of the victim. This effect is real and it affects the overall relation with other financial benefits that a person is supposed to receive, such as bank loans, and even mortgages. These deceitful claims can even destroy a person’s health policy benefits and probably leave him or her with poor or even no coverage in a medical urgent situation. This may lead to a case where a person is denied treatment or when having an expensive operation since the medical coverage could have been maxed out completely (Gerard, Hillison & Pacini, 2004).
There is also another case where the wrong information recorded because of the fraud could involve the wrong blood type or even a certain medicine category that a person is allergic to, and when going for medical attention one may receive a wrong prescription, something that will be putting the life of a person on line, particularly in times of an emergency. Finally, long term effect of having false medical claims is a result where an individual is being denied of health insurance in the future. This can also take the projection of health insurance claims being dramatically increased (Slosarik, 2002).
Dealing with Medical Identity Fraudsters
- Checking the benefit explanation frequently, especially when getting them from the insurer. This may involve being sure that such information consists of a doctor who has been providing treatment and other services, and if anything is not right as expected, always sound an alarm to the insurer before it is too late.
- Get in contact with the insurer to make sure that a yearly statement is issued out for cross checking, particularly over the listing all benefits paid out in relation to the stated medical policy. The cross checking should involve the process of checking any irregularities to be reported.
- Getting a copy of all the medical records from the assigned doctor, pharmacy, hospital, and laboratory for proofing purposes, especially at times when one might be thinking that he or she is a victim of medical identity fraud.
- Ensuring that the credit reports are checked with the significant credit reporting agencies, such as TransUnion, Experian and Equifax.
- Ensuring thatany false medical reports are immediately corrected, and this can involve a process of checking with the assigned physician, medical labs, local hospitals, and any other assigned medical facility for the purpose of being sure they have correct information.
This may appear to be a daunting task to ensure that all medical information is correct and has not been altered, but it is of great significance, especially to a person’s health profile and medical benefits. Medical identity fraud has been found to be bad and can cost the life of a person. Therefore, everyone have a responsibility of ensuring that all information concerning his or her health are correctly entered and protected from any individual who may want to use them for his or her own financial gains (Gomes, 2005).
- Facebook Fraud
A million users of the internet normally find themselves on a variety of social and professional networking sites, where they all innocently and happily share lot information about their overall lives. Initially, such networking sites are developed and made popular for better reasons, such as enabling different people from varying background to connect and always keep in touch. Because of such popularity and usefulness of the sites, most of the identity fraudsters are finding their way into these websites by creating a new tool for identity fraud purposes. As a social network, facebook has recently been targeted by many fraudsters and the impact experienced over a short period of time is quite devastating, until many countries are turning out to ban the access to such sites for the purpose of security measures. To understand what is happening on facebook site in relation to identity fraud, the following aspects will be considered.
Social Networking acting as a New Venue for all kind of Frauds
Most of the well-known emails when it comes to scams have rapidly found their way onto social networking sites, and despite the fact that the same sites are working extra-harder to ensure that such scams are identified prevented, so that the misuse of their systems is limited or just brought down completely, most of the phishing scams, cons, malware are occurring on daily basis. As with other fraudsters, phishing normally attacks on social networking sites and also aim to swindle a person into granting information that is considered to be sensitive information, which in one way or another can easily be applied in stealing a person’s identity. Such tricks most of the times appears to be quite harmless, and they may be conveyed through the messaging of a social networking site or even through a good looking application.
Similar to this, some emails or unknown applications have been found to contain malware, which is a code that is designed to cause harm to the computer if the malware within the application or email is downloaded. The goal of having all of this is to tack all activities taking place on the computer that will provide a chance to such fraudsters to have access to passwords and identity documents for generation of financial accounts. Recently, there has been a con of Facebook, where a fraudster assumes a person’s online identity and keeps on sending out pleas that are desperate for the purpose gaining sympathy from other over financial gains. The users have been warned about such cons but still the problem is going on and people are becoming victims of fraud schemes (Kerley & Copes, 2002).
Fraudsters impersonating a person in target of his or her friends
This scam is considered the most disturbing part of the fraud between the identity theft and networking sites, as it is a form of trusted-friend-based swindle. It is considered to be a disturbing form of fraud since everyone is wary of the existing malware and phishing scams that normally uses facebook and other social networks for the purpose of stealing and robbing off individuals their identity. They achieve this impersonation by hacking into the account and trying as much as possible to spam the network, or even they do it through other means by creating new credit accounts in the victim’s name to gain access to others for any financial gain. By following the report posted most of the security experts concerning social and professional networking sites, it is pointed out that many people have posted a lot of information and personal details that puts their identity at risk of impersonation by other people, and this has proved to be quite dangerous (Stafford, 2004).
Protecting against Facebook Fraud
The main purpose of any social or professional networking sites is not to fraud people, but these sites have become the most target sites for fraud activities, as they are sites that have millions of users. Therefore, every user of social or professional networking sites should use the following measures as a first step in protecting him or herself, and the end protecting those who are closer, such as family members, workmates and friends (Newton, 2004).
- Frequently review the account privacy settings for the purpose of making sure that all the information posted is only shared between the people that can be identified.
- All communications received from friends, family members, or even colleagues that use social or professional networking sites should be treated with the same healthy uncertainty that is normally applied to other forms of communications, such as phone messages and email.
- Consider trying to detect any form of quizzes or surveys that are posted on such sites by the help of the identity protection service, such as ProtectMyID&™.
- Synthetic Identity Fraud
This kind of fraud takes place when an individual with motives of stealing gets bits of information from different identities and designs his or her own identity by putting all of them together. This normally takes place when the social security number of a victim is applied together with a different name and also a different date of birth. As it may sound, it is quite difficult to discover this person as all information incorporated is quite mismatched; hence it is a fraud that can take years before it is even detected. The fraudsters normally open new bank accounts, apply for a new job, or even apply for new credit cards, and he or she may achieve this by using the social security number, which is the only information that is identical to one person. The reason why this form of theft can go on a long period before it is discovered is that the new accounts created and action carried out through this forgery normally don’t show up on real credit report of a victim (Lacey & Cuganesan, 2004).
Conclusion
The concern of this kind of fraud is that it becomes a serious issue when the stolen social security number finds its way into databases that is basically designed to flag all kinds of criminals, and this can be done through a background check. The resultant to such checks and identification is that one will be accused of a crime that he or she did not commit. Just for the reason that it has a different name that is attached to the exact social security number does not prove the innocence of a person automatically, as one will be indicted for being in possession and using an alias for documentation purposes. In case one becomes a victim of Synthetic identity fraud, here are some of the things that can be done to find out the issues behind the fraud (Leary, 2005).
Possible Recommendation
- Be careful in reviewing the yearly Social Security statement by making sure that there no more income accounted than the really earned amount.
- Being wary of many emails received in another person’s name as this can indicate some forgery going on out there.
- Ensure that the credit reports are reviewed regularly, as this will help in checking for any form of possible imprecise information and any illegal financial records.
- Incase credit is denied, it is always irrational to find out if the lender made such a decision basing everything on the existing personal credit information and also personal identity, and this should not in line someone else as it may cause a lot of problem.
- Regard taking time and resources to investing in the existing identity theft protection services, which will have the mandate to monitor the provided personal credit information. Such product assists in searching the Internet for illegal utilization of the Social Security number, debit cards and credit cards.
As a word of caution and understanding about frauds, it is always of significance for everyone to know the kind of frauds that exist and how they are committed, as this will assist in coming up with strategies that will protect the most crucial and targeted information from the fraudsters. The following list gives a highlight on how the most prominent frauds may be committed.
- Cases of Phishing
- Having counterfeit checks
- Cost allocation that is quite improper
- Cases of Spyware
- Mishandling of the existing government contracts
References
Best, R. A., 2004, Identity Theft: A Legal Research Guide. Buffalo, New York: William S. Hein & Co.
Manz, W. H., 2005, Federal Identity Theft Law: Major Enactments of the 108th Congress, Buffalo, New York: William S. Hein & Co.
Menninger, K., 2005, Identity Theft and Other Misuses of Credit and Debit Cards, American Jurisprudence Proof of Facts 3d, 81:113.
Newton, M., 2004, The Encyclopedia of High-Tech Crime and Crime-Fighting, New York: Checkmark Books.
Allison, S. F. H., Schuck, A. M., & Lersch, K. M., 2005, Exploring the Crime of Identity Theft: Prevalence, Clearance Rates, and Victim/Offender Characteristics, Journal of Criminal Justice, 33(1), 19.
Gerard, G. J., Hillison, W., & Pacini, C., 2004, Identity Theft: The US Legal Environment and Organizations Related Responsibilities, Journal of Financial Crime 12(1) 33.
Hayward, C. L. (Ed.)., 2004, Identity Theft. Hauppauge, New York: Novinka Books.
Katel, P., 2005, Identity Theft. The CQ Researcher Online, 15(22), 517-540, Retrieved 12/08/2011 from http://library.cqpress.com/
Lacey, D., & Cuganesan, S., 2004, Colloquium on Identity Theft: The Role of Organizations in Identity Theft Response: The Organization-Individual Victim Dynamic, The Journal of Consumer Affairs, 38(2), 244.
Leary, T. B., 2005, Identity Theft and Social Security Numbers. Electronic Banking Law and Commerce Report 9:10.
Miller, S. F., 2003, Someone Out There is Using Your Name: A Basic Primer on Federal Identity Theft Law. Federal Lawyer 50(1): 11.
Slosarik, K., 2002, Identity Theft: An Overview of the Problem. Justice Professional 15(4):329-343.
Sovern, J., 2003, The Jewel of Their Souls: Preventing Identity Theft Through Loss Allocation Rules. University of Pittsburgh Law Review, 64:343-406.
Stafford, M. R., 2004, Identity Theft: Laws, Crimes, and Victims, The Journal of Consumer Affairs, 38(2): 201.
Sullivan, B., 2004, Your Evil Twin: Behind the Identity Theft Epidemic, Hoboken, New Jersey: John Wiley & Sons.
Towle, H., 2000, Identity Theft: Myths, Methods and New Law, Rutgers Computer and Technology Law Journal 30: 237.
Brenner, S., 2004, U.S. Cybercrime Law: Defining Offenses, New York: Information Systems Frontiers 6:2:115-132.
Davis, K., 2005, Can You Smell the Phish? Kiplinger’s Personal Finance 59(2): 76-80.
Gomes, L., 2005, Phisher Tales: How Webs of Scammers Pull Off Internet Fraud. The Wall Street Journal B:1.
Collins, J. M., & Hoffman, S. K., 2003, Identity Theft First Responder Manual for Criminal Justice Professionals: Police Officers, Attorneys, and Judges, Flushing, New York: Looseleaf Law Publications.
Kerley, K.R. & Copes, H., 2002, Personal Fraud Victims and Their Official Responses to Victimization, Journal of Police and Criminal Psychology, 17(1), 19-35.
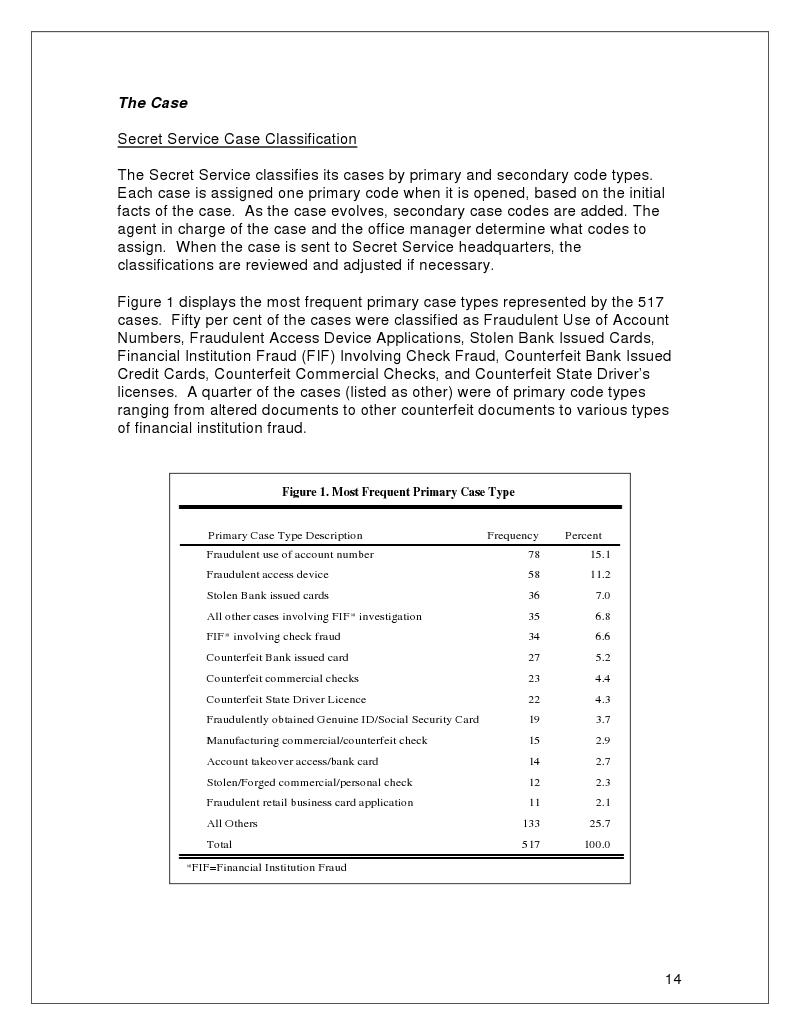
Appendix 1: Most Frequent Primary Case Type
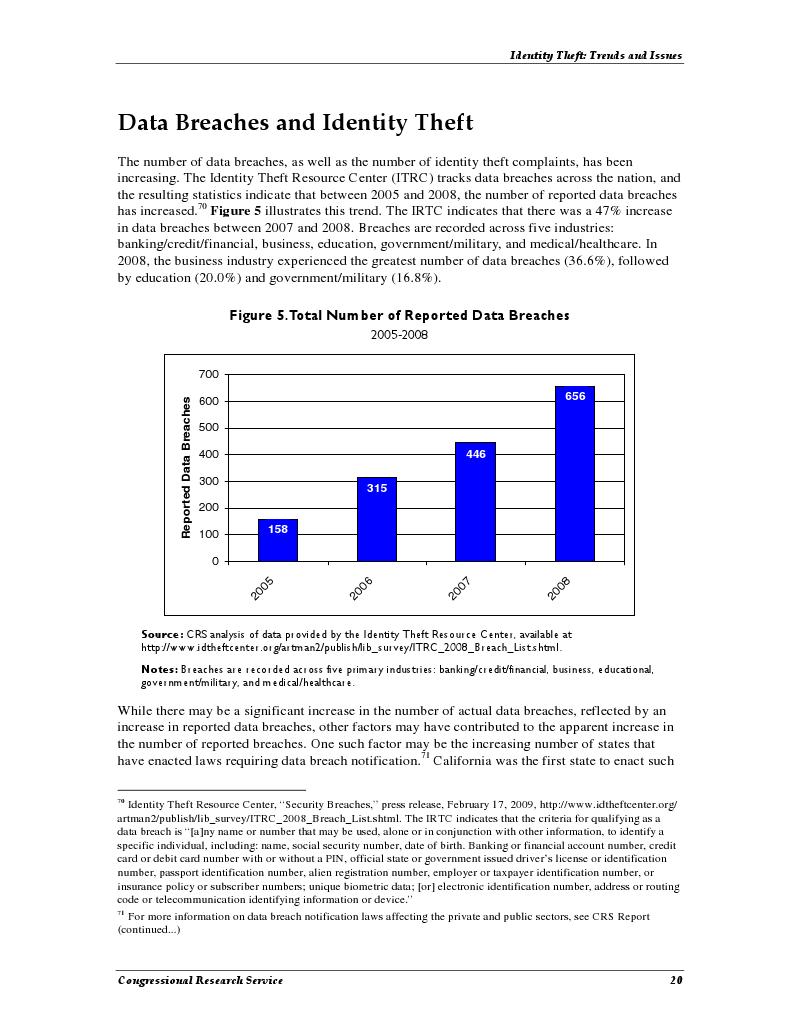
Appendix 2: Data Breaches and Identity Theft